I recently purchased an Amazon Echo to do some research and gain some more experience in the IoT space. Looking around, there has been some interesting work done in assessing the Echo for vulnerabilities, traffic analysis, rooting the device, and more. Though I haven't had a ton of success yet in finding issues, I did find a bit of useful information that may help others and myself.
Reading through other's blog post, a common issues seems to be capturing and accessing the Echo's traffic. Somebody analyzed the browser-based Echo setup process. Another intercepted Echo traffic using an iptables and DD-WRT to intercept firmware updates. It was the latter article by @micaksica that really peaked my interest. I replicated the steps in the post, so I'm analyzing the firmware now (which will be for another post maybe). I'm new to ARM assembly and APK decompiling, but I'm reading a book and some tutorials :) Moving on...
What peaked my interest about this post was capture Echo's HTTPS traffic. In Wireshark, the majority of the traffic is TLS 1.2 encrypted (as of this post). I would read the article for more information, but long story short Echo didn't want to play nice when proxying TLS connections.
However, I believe I found a workaround to this issue. The Amazon Alexa software comes installed by default on the Kindle Fire Tablets. To my knowledge it's the same software on the Echo itself, especially when looking at an older Echo firmware update, it showed that the OS version is ro.build.version.fireos=5.5.0.3. Echo used Kindle Fire OS.
Using the Kindle Fire tablet, you can setup the device to proxy app traffic through Burp. Alexa is now just another app on the device. When Alexa is triggered or performs any action I get the traffic through Burp, bypassing the need to deal with secure communications or get the Echo device to play nice with my CA. Alexa and Burp are now friends :)
To showcase a bit of this I wanted to show an "exchange?" that takes place when asking Alexa something like "what is the weather?".
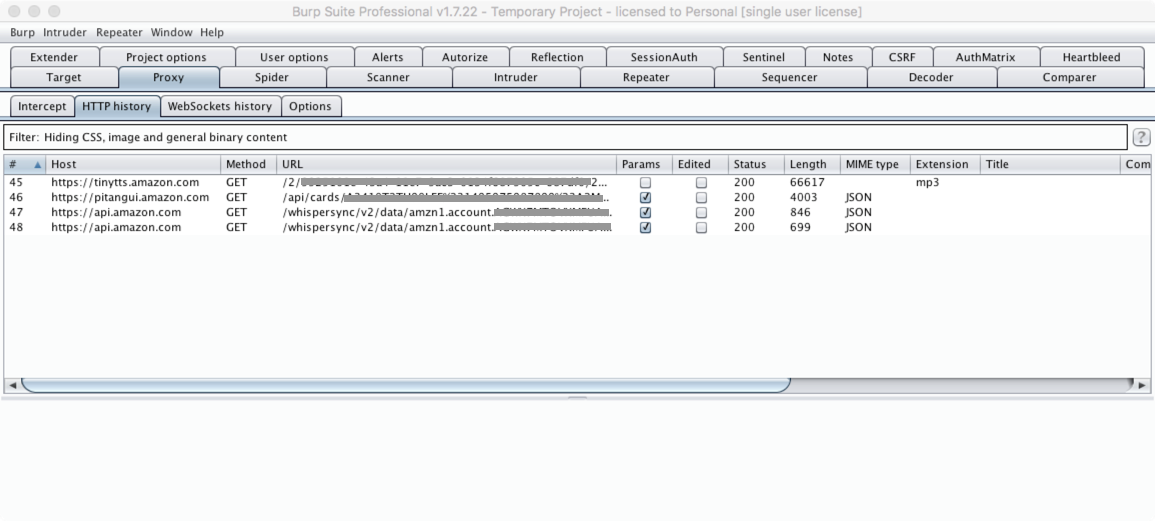
One really interesting thing about this is the call to https://tinytts.amazon.com/. If you follow that link, it contains the Alexa response in .mp3 format. However, it looks like those files exist for awhile, if not days. This makes me wonder if the responses are stored forever, and if it is possible to capture responses from other users.
Anyway, that's all I have right now. I figure somebody would find this useful and it'll help them in researching this device.